A lapse in security has led to the leaking of over a hundred thousand Aadhaar numbers, TechCrunch can reveal.
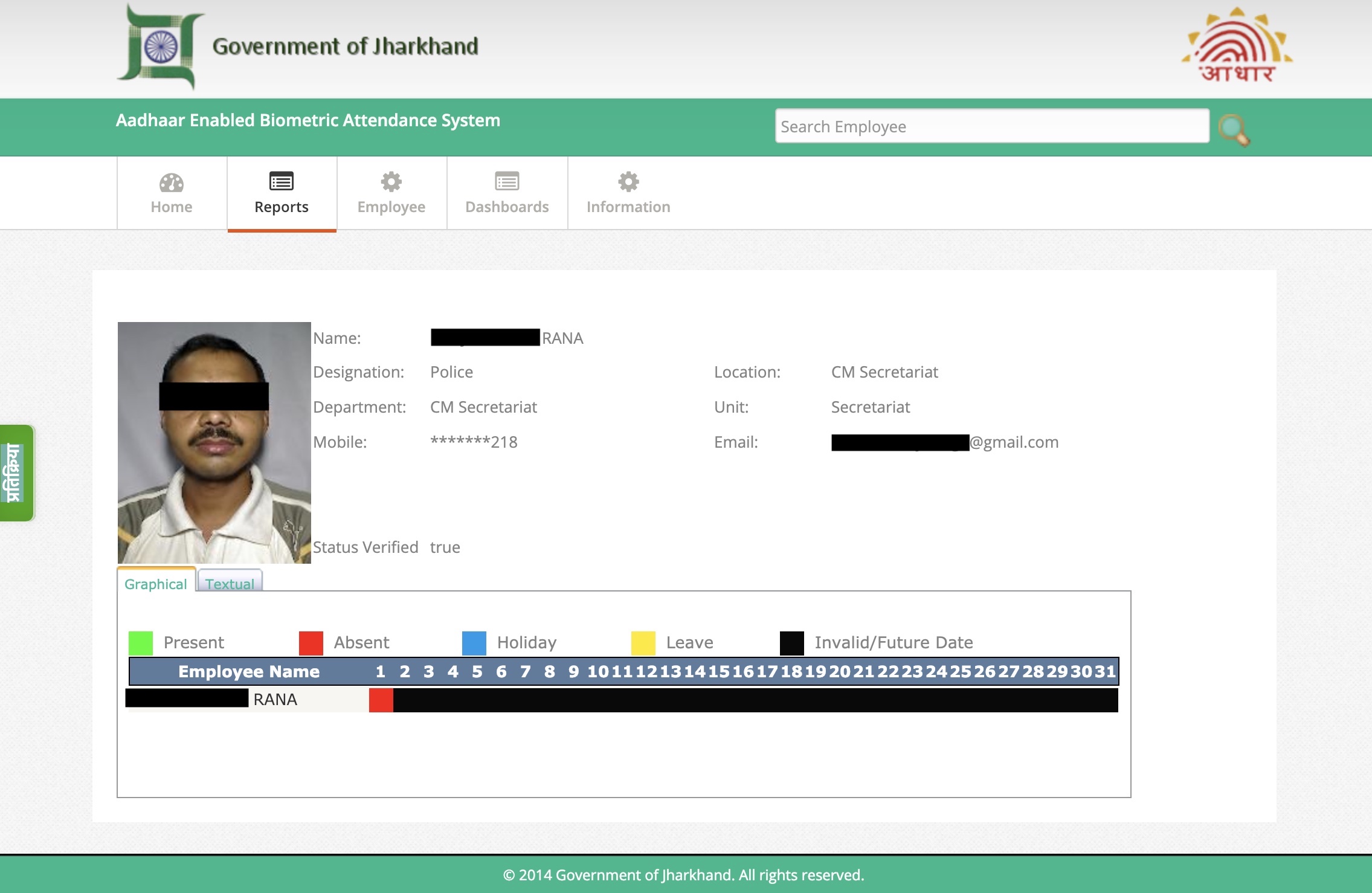
One of the web systems used to record attendance of government workers for the Indian state of Jharkhand was left exposed and without a password as far back as 2014, allowing anyone access to names, job titles, and partial phone numbers on 166,000 workers as of the time of writing.
But the photo on each record page used the file name as that worker’s Aadhaar number, a confidential 12-digit number assigned to each Indian citizen as part of the country’s national identity and biometric database.
The data leak isn’t a direct breach of the central database run by Aadhaar’s regulator, the Unique Identification Authority of India (UIDAI), but represents another lapse in responsibility from the authority charged with protecting its data.
Aadhaar numbers aren’t strictly secret but are treated similarly to Social Security numbers. Anyone of the 1.23 billion Indian citizens enrolled in Aadhaar — more than 90 percent of the population — can use their unique number or their thumbprint to verify their identity in order to enroll in state services, like voting, welfare or financial assistance. Aadhaar users can even use their Aadhaar identity to open a bank account, get a SIM card, call an Uber, buy something on Amazon, or rent an Airbnb.
But the system has been plagued with problems that have led to starvation in cases, and the illicit trade of citizen data on the underground market.
It’s unclear why the Jharkhand government site was accessible to anyone who knew where to look, but little effort had been put in to ensure the security of the system — or even hide it from the outside world. The site was easily found on a subdomain of the state government’s website, but for long enough that it was indexed by Google, which cached copies of not only the site itself, but also its attendance record pages that still contain Aadhaar numbers in each worker’s photo.
TechCrunch asked Baptiste Robert, a French security researcher who goes by the online handle Elliot Alderson, to take a look at the site. Robert has prior experience in revealing Aadhaar-related data leaks. Using less than a hundred lines of Python code, Robert demonstrated that it was easy for anyone to scrape the entire site in batches to download their photos and corresponding Aadhaar numbers.
TechCrunch verified a small selection of Aadhaar numbers from the site using UIDAI’s own verification tool on its website. (We used a VPN in Bangalore as the page was unavailable in the U.S.). Each record came back as a positive match.
After confirming our findings, we reached out to both the Jharkhand government and UIDAI.
Jharkhand’s attendance site leaking worker data. (Image: TechCrunch)
At the time of publication, neither had responded, but the website had been pulled offline.
The exposure may represent a fraction of the billion-plus users registered with Aadhaar, but uncovers yet another inadvertent disclosure of citizen data from a system that UIDAI claims is impenetrable. Instead of learning from mistakes and mishaps, UIDAI instead has shown a long history of rebuffing evidence of security incidents or breaches with mockery and declaring findings as “fake news,” by claiming to refute evidence without presenting any of its own.
The leak of Aadhaar numbers may not be seen as sensitive compared to leaked biometric data. Former attorney general Mukul Rohtagi once called a separate leak of Aadhaar numbers “much ado about nothing.” But it’s raises fears that obtaining and misusing someone’s number could lead to identity theft and fraud — which reportedly peaked last year.
Others have expressed concern that the system puts privacy at risk by recording information on a person’s life, which authorities can use to conduct surveillance on ordinary citizens.
But the exposure alone contradicts the Indian government’s claims that the Aadhaar system as a whole is secure.
In recent years, several security lapses involving data relating to Aadhaar have reignited fresh concerns about the centralized database — including several issues found by Robert. Last year, security researcher Karan Saini, a New Delhi-based security researcher, found a poorly-secured web address used by state-owned utility company Indane that had direct access to the Aadhaar database, allowing him to query results from the system. UIDAI rubbished the reports, baselessly claiming that there was “no truth to this story” in a series of tweets from its official Twitter account, despite evidence to the contrary. In the same year, India’s Tribune newspaper reported that some were selling direct access to the Aadhaar database. UIDAI responded by filing a complaint against the reporter with police.
Despite the security concerns, India’s Supreme Court ruled the database constitutional in September after a long-running court battle.
Got a tip? You can send tips securely over Signal and WhatsApp to +1 646-755–8849. You can also send PGP email with the fingerprint: 4D0E 92F2 E36A EC51 DAAE 5D97 CB8C 15FA EB6C EEA5.
from TechCrunch https://tcrn.ch/2WuRc7X
No comments:
Post a Comment